Power analysis based software reverse engineering assisted by fuzzing II
3. September, 2020 #embedded security #secforcars #power analysis #reverse engineering #fuzzing #attacks
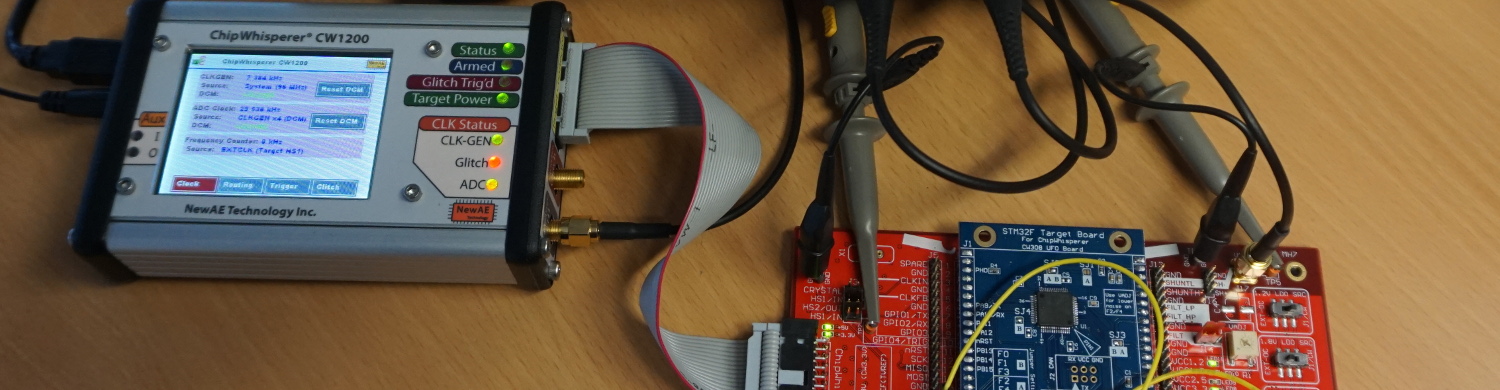
In the previous post a setup and a technique to extract a representative section of a powertrace of a specific instruction of a STM32F3 processor were described. This section is called a “template”. These templates should later be used to identify instructions via a power sidechannel and reconstruct the flow of an unknown program on a controller that can not be dumped via JTAG. In this part of our poweranalysis series the extracted templates from the previous post will be analyzed to determine whether they are representative enough to reverse engineer entire programs from a powertrace.